Bitcoin has redefined what it means to possess and transfer value, in that the value is no longer entrusted to a 3rd party, e.g. a financial institution, and is instead based solely on the cryptographic keys (“keys”) possessed by the owner or controller of that value. While it is substantially liberating to not require 3rd parties to effect transfers of value, this liberty comes with a substantial increase in personal or organizational responsibility on part of the party that controls the keys that correspond to that value. In order to spend bitcoins, one must create a transaction signed with one or more of these keys on some kind of computer hardware, whether it’s a desktop computer or a calculator-like device. Compromise of the hardware or software that handles these keys could lead to immediate irrevocable theft of the funds they correspond to, which is a much worse failure mode than what could happen with funds stored at a typical financial institution.
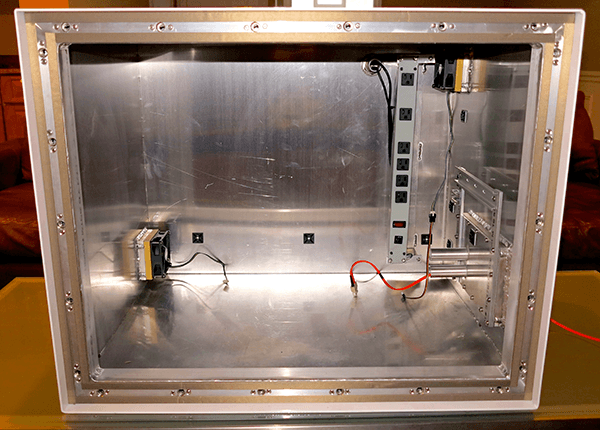
Put bluntly, this means “if you get hacked, your funds are gone”, a rather serious and hopefully avoidable failure scenario. Taking a note from military and intelligence services, I felt that it made sense to electromagnetically isolate hardware used to handle Bitcoin keys from their surroundings to reduce their attack surface. Conveniently enough, this problem has already been addressed for the past several decades by a number of companies, so I contacted LBA Group about making a customized version of an existing Faraday cage they manufacture, the EMFaraCage FC-10S. The customized cage has filtered 110V power, an internal power strip, intake and exhaust fans and can hold 2 desktop computers.
There are a number of existing countermeasures that can be taken by a security-conscious bitcoin holder to prevent compromise of their keys. These countermeasures include but are not limited to:
- using cold storage to store keys offline
- splitting up keys in cold storage to compartmentalize their value, e.g. separate offline wallets with BTC 100 in each of them
- using multi-signature transactions to avoid relying on the security of a single machine
- using a device that is duty-built with reduced functionality, e.g. a TREZOR
These are all effective countermeasures, but in every case they involve connecting to a computer, which may or may not be compromised, either at the software, firmware or hardware level. Ultimately, the security of your bitcoins is based on assumptions made about the security of software, firmware and hardware that are part of the computers being used.
Having the ability to completely and thoroughly audit the software, firmware and hardware one uses is far outside the capabilities of most individuals and organizations. If you are running a closed source OS, you cannot inspect the source code at all, and if you’re running an open source OS, you cannot be certain of the security of the code, even when it is open source. Firmware for peripherals is almost always closed source despite efforts to open source firmware in a number of cases, e.g. the OpenSSD Project. Almost everything except the simpler hardware components have closed source designs, and the circuits use such small-scale processes that it is challenging to even image the circuits, much less audit them. In many cases, modern Intel CPUs include a 3G antenna as a side channel for remote access and administration. It is simply not possible for anyone but a very well-funded organization to be reasonably certain their machines have no firmware or hardware backdoors or bugs that lead to compromise via a number of side channels, e.g. electromagnetic (“EM”), electro-accoustic, and accoustic emissions.
The good part about these side channels is that the EM side channel is relatively straightforward to secure using a Faraday cage. While a Faraday cage is based on the relatively simple concept that the interior of a closed surface made of an ideal conductor has zero electric field, the real-world construction of a Faraday cage requires a fair deal of attention to detail in selection of the conductors and their assembly. LBA Group offers cages that have an average attenuation of 50 dB for EM waves over the frequency range of 10 kHz to 6 GHz, meaning that the EM emissions of these frequencies are reduced in power by a factor of 100,000, i.e. 10^5. The particular model I had them customize, the EMFaraCage FC-10S, was fitted with intake and exhaust fans, a filtered power supply and an internal power strip so that up to 2 machines can be running inside it while closed. It also has 2 waveguide ports to allow fiber cables to penetrate the enclosure.
It is worth noting that a consequence of using a Faraday cage is that you cannot have any normal ethernet cables penetrating the cage, since this would “break” the EM isolation of the cage. This means that you must use ethernet-to-fiber converters or fiber network cards for the machines inside the cage. The potential complexities of fiber converters makes it clear that the ideal situation is to have a room-sized Faraday cage and only require fiber where network penetrates the room, but this is often more expensive than buying a portable cage and is a fixed install.
If you are interested in having your own EMFaraCage or similar manufactured by LBA Group, please contact Byron Johnson at bjohnson@lbagroup.com and feel free to reference this blog entry and this particular cage configuration.